Information Security as a Service
Information Security as a Service
Not One Universal Solution
We are here to customize a cyber security plan that meets your needs.
Cyber Security
Cyber Security as a Service
Do you need your system tested for vulnerabilities and weaknesses? Have you secured your systems but are missing policies and other pertinent documents? Are your annual or quarterly security assessments running properly?

WE DO THIS AND MORE
Information Security as a Service
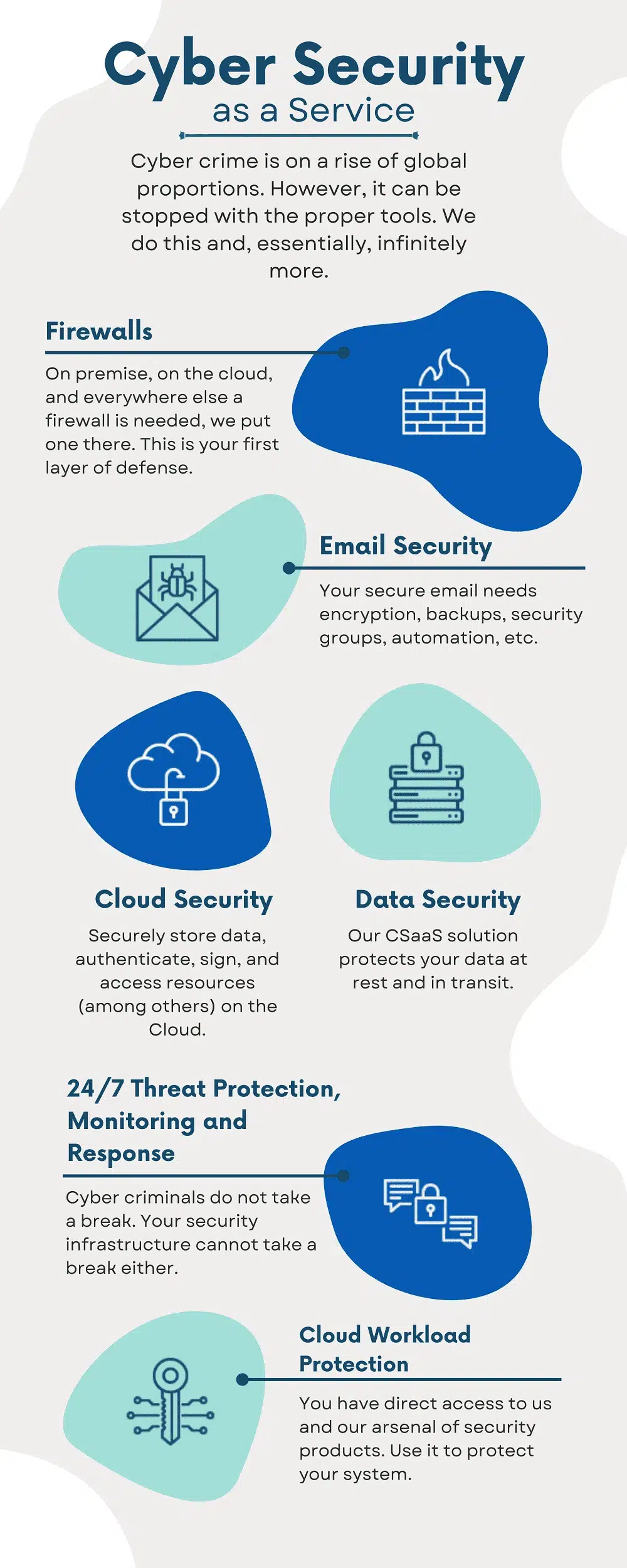
Cyber crime is on a rise of global proportions. However, it can be stopped with the proper tools. We do this and, essentially, infinitely more.

Firewalls
Information security as a service gives your company its required security posture without having to overspend on fluff.

Information Security as a Service Email Security
Your secure email needs encryption, backups, security groups, automation, etc.

Cloud Security
Securely store data, authenticate, sign, and access resources (among others)
on the Cloud.
on the Cloud.

Data Security
Our CSaaS solution protects your data at rest and in transit.

24/7 Threat Protection, Monitoring, and Response
Cyber criminals do not take a break. Your security infrastructure cannot take a break either.

Cloud Workload Protection
You have direct access to us and our arsenal of security products. Use it to protect your system.

Asset Protection
No one without proper permissions should have physical access to an organization’s information systems.

BDR Compliance
Because nothing can prevent a disaster (hence the name), all organizations can do is prepare for ...

Business Continuity
The most important reason to find a perfect BDR (Backup and Disaster Recovery) solution is to have..

Cloud Protection
Many employees work remotely. Organizations with remote workers have offloaded their systems to the Cloud.

Health Information
Every year, around 1,085,783 doctors see about 65,440,000 patients 883.7 million times in the United States.

Data Security
First, information is data that has been converted to have meaning. Therefore, all information is based on data.

IT Governance Architecture
How does IT work for your business? In short, that is the question IT Governance can answer.

Pen Testing
Penetration testing or ethical hacking is testing an organization’s systems for exploitable..

Security Risk Assessments
A security risk assessment identifies, assesses, and implements
key security..
key security..

Security Architecture
Security Architecture is the blueprint (pun intended) to your company’s information systems. A company’s information

Secure Integrations
Today, applications integrate with others through JSON, GraphQL, Falcor, Blockchain, etc.

VPN Security
It is well known by the security community, among others, that Internet was designed without security.

Security Mentality
Securing PCs and some printers is not a solution anymore. Today, tablets, phones, IoT, blockchains, virtual networks, among others, need to be secured.
Best Required Standards
Compliance Readiness Arsenal of
Security Tools
The security tools you use must meet required standards.
You cannot be assessed without
Compliance Readiness. We use any required tool to secure your environment.
Compliance Readiness. We use any required tool to secure your environment.









Ready To Secure Your Assets?
We are here to help when an incident happens. Be proactive, and call us before it happens to save you money and your business.