Information Security as a Service

Information Security as a Service
Not One Universal Solution
We are here to customize a cyber security plan that meets your needs.
Customized Security Stack
Security is not a one-size-fits-all solution. Do not listen to anyone that tells you otherwise.
Cyber Security
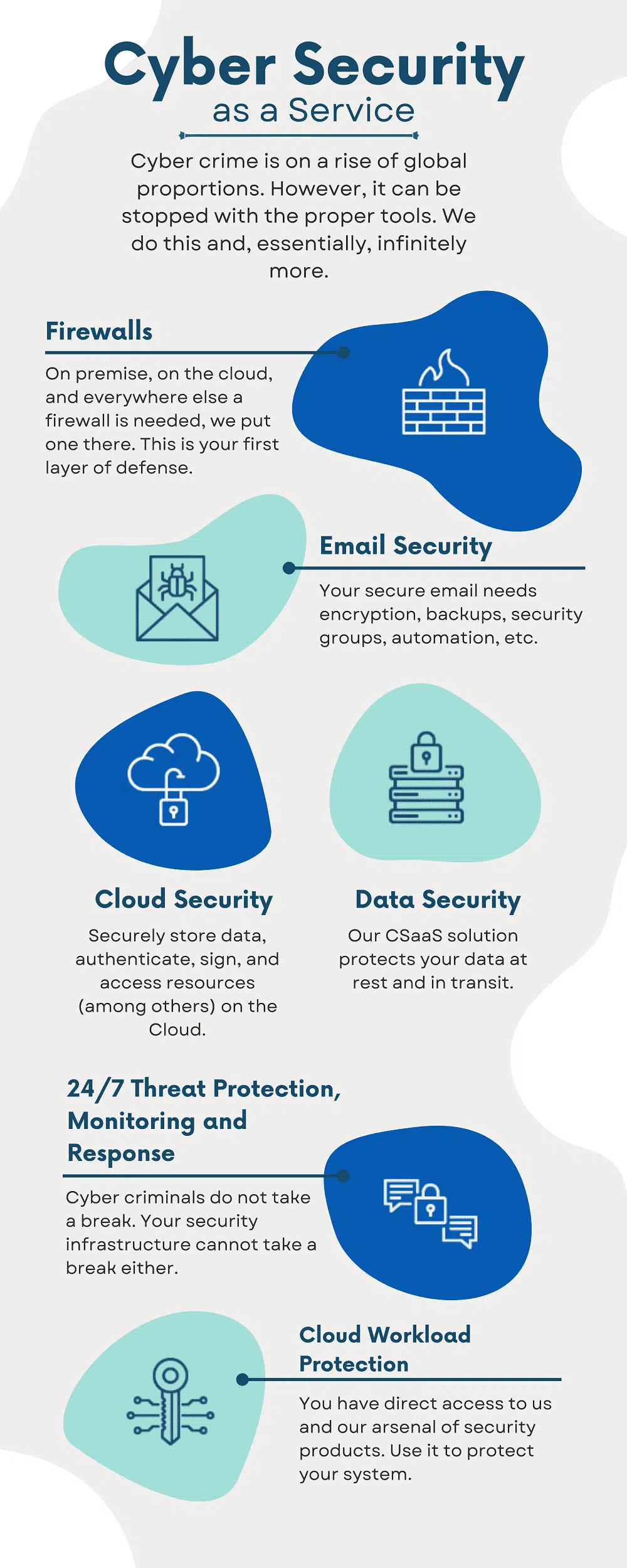
Cyber Security as a Service
Do you need your system tested for vulnerabilities and weaknesses? Have you secured your systems but are missing policies and other pertinent documents? Are your annual or quarterly security assessments running properly?

WE DO THIS AND MORE
Information Security as a Service
Cyber crime is on a rise of global proportions. However, it can be stopped with the proper tools. We do this and, essentially, infinitely more.
Firewalls
On premise, on the cloud, and everywhere else a firewall is needed, we put one there. This is your first layer of defense.
Information Security as a Service Email Security
Your secure email needs encryption, backups, security groups, automation, etc.
Cloud Security
Securely store data, authenticate, sign, and access resources (among others) on the Cloud.
Data Security
Our CSaaS solution protects your data at rest and in transit.
24/7 Threat Protection, Monitoring, and Response
Cyber criminals do not take a break. Your security infrastructure cannot take a break either.
Cloud Workload Protection
You have direct access to us and our arsenal of security products. Use it to protect your system.

Asset Protection
BDR Compliance

Business Continuity

Cloud Protection

Health Information

Data Security

IT Governance Architecture

Pen Testing

Security Risk Assessments

Security Architecture

Secure Integrations

VPN Security